Development and Implementation of Centralized Monitoring and Management System of Repeater Based on MapXtreme
As a relay product, the repeater used in cellular mobile communication can ensure wireless network coverage without increasing the number of base stations, and has the advantages of simple structure, low investment, and easy installation. It can be widely used in wireless signals. Covered blind areas and weak areas are a preferred solution to achieve the goal of "small capacity and large coverage". In order to ensure the safe and reliable operation of the repeater station, centralized monitoring of the repeater station equipment must be carried out, real-time acquisition of various working parameters of the equipment, synchronous alarm when a failure occurs, and parameter adjustment according to actual needs.
As the construction scale of repeater stations expands, it is necessary to introduce electronic maps in the centralized monitoring and management system to graphically display the geographical distribution of repeater stations and the relationship between base stations and other main equipment for monitoring personnel. Provide a more intuitive and convenient operation interface. Building a centralized monitoring and management system for repeaters based on MapXtreme is a feasible solution to achieve this goal [1].
1 System Architecture MapXtreme-based repeater centralized monitoring and management system is a comprehensive network management system that integrates wireless communication technology, data communication technology, dynamic data processing technology, computer technology and GIS technology. The station provides multiple functions such as real-time setting, query, data transmission, and distress alarm, etc., providing operators with a complete set of automated remote communication monitoring services.
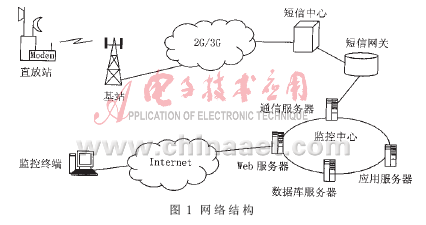
1.1 The network structure system adopts a distributed architecture design, and its network structure is shown in Figure 1. The monitoring equipment in the repeater sends the monitoring parameters in the form of SMS through the wireless modem. After receiving the signal, the base station sends it to the SMS center via the 2G / 3G mobile communication network, and then the SMS gateway reaches the monitoring center. The monitoring center consists of multiple servers located in the same local area network. Among them, the communication server is responsible for sending and receiving information from the short message center; the application server is responsible for the realization of various management business functions in the system; the Web server is responsible for connecting to the Internet to provide a maintenance interface for monitoring personnel; and the database server is responsible for querying and managing various types of data. Each monitoring terminal connects to the server via B / S via the Internet to obtain monitoring information and implement related operations [2].
1.2 The communication protocol structure system contains multiple physical entities, such as repeaters, short message centers, monitoring centers, and monitoring terminals. In order to ensure reliable communication between entities, the layered principle is used here to divide the communication protocol, clarify the interface form between layers, reduce the mutual interference between layers, and realize the modular design of software. The entire communication protocol is divided into 4 layers, as shown in Figure 2. From the bottom layer to the top layer are: bearer layer, access layer, network layer and monitoring application layer [3].

(1) Bearer layer: It is the actual link for communication. This layer can provide byte-oriented data packets to the access layer. In addition to supporting SMS connections, it also supports RS-232, RS-485 and Ethernet. This layer protocol Referred to as TP.
(2) Access layer: Define the communication transmission channel and related requirements, in order to achieve information intercommunication with various media, and bear and ensure the reliable transmission of network layer protocol data. This layer protocol is referred to as AP for short.
(3) Network layer: It carries the monitoring application layer protocol package to achieve the isolation of the monitoring application layer from the communication link and network structure, and can provide the monitoring application layer with the monitoring instructions and data that the device needs to process. This layer protocol is called NP for short.
(4) Surveillance application layer: Aiming at various monitoring functions and implementing data organization for monitoring functions, the protocol of this layer is called MAP for short.
1.3 Management function structure The management function of the system is divided into 5 major modules: system management, repeater information management, task management, alarm management and statistical analysis, as shown in Figure 3.
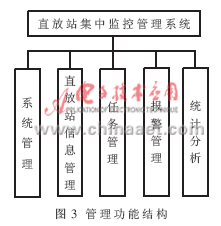
(1) System management module: mainly completes user and authority settings, device parameter editing, various log acquisition and export operations, transmission service startup and shutdown, real-time display and deletion of task lists, system testing, etc.
(2) Repeater information management module: mainly complete project list viewing, site query, monitoring object management, associated assignment configuration, electronic map browsing, etc. Because the monitoring center needs to realize the association between the near end and the far end of the repeater, the association between the near end and the base station of the repeater, the correspondence between the master device and the related slave devices, and the correspondence between the repeater and the associated cell, so in the electronic Topological relations should be presented on the map.
(3) Task management module: mainly completes the display, editing and setting of the task list. The task list displays information about communication tasks added by the user, including: task sequence number, task name, communication function, transmission mode, effective time, expiration time, whether it is effective, etc.
(4) Alarm management module: It can realize real-time collection and centralized monitoring of alarm data, assist operation and maintenance personnel to quickly find network problems and locate faults, automatically generate alarm work orders, and provide various processing functions for alarm information. Statistics and query function of historical alarm information.
(5) Statistical analysis module: it can complete the analysis of the relationship between the downlink input, output power and downlink standing wave, count the alarm information of each site, check the pairing of near and far devices, analyze whether the parameter objects of the site are complete, and whether the various thresholds meet Requirements etc.
2 Analysis and design of the MapXtreme application solution The introduction of electronic maps in the centralized monitoring and management system of the repeater can accurately locate the position of the repeater and correlate it with the position information of the base station, develop the correlation function of the alarm, and can provide more intuitive User interface for easy monitoring and operation.
Electronic map function can be realized through MapXtreme in WebGIS system. MapXtreme is a map application software developed by MapInfo based on Internet technology. Among them, MapXtreme for Java version is a 100% pure Java product, which has the characteristics and advantages of cross-platform, componentization, object-oriented, and J2EE compliance, so it is selected as Development Platform. Using MapXtreme to develop WebGIS applications, developers can centrally control and maintain map and database data, and centrally implement map application functions. In addition, the use of the IE browser as the client's user interface allows developers to closely integrate the geographic information system with other systems to provide users with a unified and complete comprehensive information service. The WebGIS application scheme based on MapXtreme is shown in Figure 4 [4].
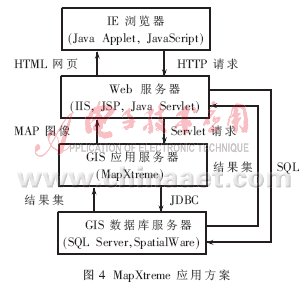
IE browser is a graphical user interface, which uses Java Applet and JavaScript to provide users with the basic operation of maps, and realizes the functions of spatial data display, query statistics and analysis.
The Web server processes the client's request and passes the spatial data processing commands to the GIS application server, returns HTML files and Java server object components; loads spatial data, etc. The client-side Java Applet reconstructs the URL class through the URL of the server-side Servlet, and sends a request to the server-side Servlet. The Servlet calls the JDBC driver. The JDBC driver is responsible for connecting and operating the GIS database and displaying it in the client's browser. The Web server layer can also directly use the standard SQL language to access the database server to obtain more complex attribute data.
The GIS application server processes the spatial data operation commands from the Web server, performs map generation and operation, etc., and simultaneously outputs the map operation results in the form of pictures to a specific directory of the Web server.
The GIS database server is managed by SpaTIalWare. SpaTIalWare is the latest spatial database management software launched by MapInfo. Its main function is to store complex MapInfo map objects in a large database and establish spatial data indexes for it, so as to realize attribute data and spatial graphic objects on the database server. Unified management of data.
3 Research and development of key technologies The WebGIS application solution based on MapXtreme has the characteristics of platform independence and balanced and efficient computing load. It uses Java technology to develop Java Servlet programs on the server side. MapXtreme is connected to the Web server as a Servlet, and provides map objects, attributes, and methods that can be used by the program scripting language to the application through the map engine. The key technologies involved in the development are the following.
3.1 Realization of the communication between the client and the server The communication between the client and the server is done through the HTTP protocol. All HTTP communications use 8-bit characters to ensure the secure transmission of binary encoded files. The system uses a processing method called tunneling. The tunnel can be seen as a channel: it uses the existing communication channel HTTP and creates a sub-protocol in it to perform special tasks. The sub-protocol to be created here will contain all the necessary information, which is used to create an object on the Web server, call methods in this object, and return the result to the client. The advantage of using HTTP tunneling is that you can concentrate on the sub-protocol, without paying attention to how to transfer data packets between the client and the server.
There are many processes to transfer a request between the client and the server. For performance reasons, as much information as possible should be transmitted in each request / response. A complete communication between the client and the server includes the following steps:
(1) Open HTTP connection: HTTP is a stateless protocol, that is, each request is regarded as an independent entity. Therefore, a new connection must be established for each request.
(2) Initialization method request: used to describe what method is called and the parameters required by the method.
(3) Set the HTTP request header: contains the data type and length sent.
(4) Send request: send the binary data stream to the server.
(5) Read request: The target Servlet program will be called and receive HTTP request data. Servlet program is to call all necessary parameters to select the corresponding method. If this is the first request from the client, a new instance of the server object will be created.
(6) Calling method: The method will be called by the server-side object.
(7) Initialization method response: If the called method throws an exception, the client will receive an error message; otherwise, the returned type will be sent.
(8) Set the HTTP response header: Just like the HTTP request header, set the type and length of the data to be sent in the response header.
(9) Send response: The binary data stream will be sent back to the client from the web server.
(10) Close the connection.
3.2 Design of GIS database structure The reasonable construction of the database is the premise of monitoring and management. The system uses SQL Server as the GIS database, including the spatial database and the attribute database. The spatial database uses a non-relational data structure, which saves map information and geographic information of repeaters in several files in a custom format of MapInfo; the attribute database uses a relational data structure to store repeater parameter information and operations unrelated to geographic information The information is stored in several attribute tables. The spatial database and the attribute database are indirectly related, and the two are connected through a certain indexing mechanism, as shown in Figure 5.
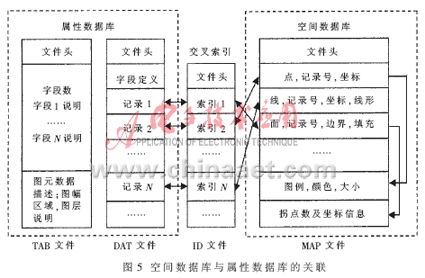
GIS data represents the spatial location of geographic entities or the geographic location of repeaters, expresses the geometric positioning characteristics of geographic entities of objects, and is expressed in coordinate data. In order to improve query and processing efficiency, the system uses a hierarchical structure to organize GIS data, that is, the map is layered according to different topics, and geographic information and repeater information are managed and stored through "layers". The layers are transparent The ways overlap and form a map. The layer is composed of primitives and attribute data, and the primitives are associated with geographic data. In this way, the map composed of layers can realize information query, data analysis and data visualization display. The data of each layer is stored in four files with the same file name and different extensions, namely TAB file, DAT file, ID file and MAP file. The functions of the four files are as follows:
(1) TAB stands for attribute data table structure file, which defines the table structure of map attribute data, including field number, field name, field type, field width, index field and some key spatial information description of corresponding layer.
(2) DAT stands for attribute data file, used to store complete map attribute data. After the file header, the table structure is described, followed by each specific attribute data record.
(3) ID stands for cross-reference file, and records the location pointer of each spatial object in the map in the spatial data file (MAP). Every 4 bytes constitute a pointer. The order in which the pointers are arranged is the same as the order in which the attribute data records are stored in the attribute data file (DAT). The cross-reference file is actually a positioning table for spatial objects.
(4) MAP stands for spatial data file, which contains spatial data of map objects, such as geometric type, coordinate information and color information of spatial objects.
3.3 Two-way query of GIS data The data query function based on WebGIS is one of the important management functions of the system, including two query methods from graph to table and from table to graph. In other words, the user can get all the attribute information of the repeater from the spatial information of the repeater on the map; at the same time, he can also get his geographic location and other geographical information through the parameters and information of the repeater.
The query from the picture to the table is through the position of the repeater's primitives to get the relevant parameters and alarm information of the repeater. The selection, positioning and control functions of the primitives in the map are only for the repeater layer, and the layer data comes from the spatial database. For the way of selecting repeater primitives, the system provides point selection and rectangular area selection functions to adapt to the operation and screening of repeaters in different situations. After the area selection, a set of repeater primitives can be obtained. The system provides the positioning function. By locating one of the primitives, the detailed geographic information and attribute information of this primitive can be obtained.
The query from the table to the graph is to query the repeater primitives that meet the conditions according to certain conditions. Using the corresponding relationship between the repeater attribute and the geographic information of the repeater, the geographic information of the repeater is obtained through the attribute information, and the repeater primitives that meet the requirements are highlighted on the map.
This paper proposes a solution for the centralized monitoring and management system of mobile communication repeater stations, which realizes the daily monitoring and management of repeater stations in B / S mode, and has a relatively complete function. The monitoring personnel can view the parameters of the repeater in the network in real time through the Web page, process the alarm, and send commands such as round robin. Figure 6 is the display interface for the client to operate the electronic map, which can complete functions such as zooming in, zooming out, moving, measuring distance, viewing basic station information and searching for stations. The implementation of the system greatly improves the operator's work efficiency and asset utilization, and reduces the operation and maintenance costs.

Shenzhen Guan Chen Electronics Co., Ltd. is a High-tech enterprise that integrates R&D, design, manufacture of computer peripheral products.The products include Thunderbolt Docking Station,USB Docking Station,USB Hubs,USB Adapter, Thunderbolt Cable , SSD Enclosure , HDD Enclosure . Our company adheres to the principle and motto of Being sincere, Responsible, Practical to meet the needs of markets and customers with high quality technology and management. We commit ourselves to new product development and also stress the exploring of international markets.
Our company owns a professional production team and establishes strict quality control standard, so we can provide high quality products and service for customers. We have Grapgic designer,3D Deisnger and Electronic designer to provides professional OEM/ODM service. Our factory covers an area of 1,000-2000 spare meters, which houses 100-200 workers, so our production capacity reaches 50,000 pieces every day.With more than 10 engineers focusing on research and development, our private model attracts much among different markets. Over 100 new designed models are released per year.There are also 3 lean production lines to fullfill small quatity orders production for variety of models.
Our Thunderbolt 3 Docking Station has passed thunderbolt certified by intel and apple.Our product also all can meet with CE, RoHS, UL, FCC and other related certification.And our factory also meets legal environmental standards ensuring your order is delivered. We have a very good reputation at home and abroad. Our products are mainly exported to Europe, USA and Southeast Asia. We provide one-stop-service and promote customers achieve rapidly development. Customer comes First, Quality Ranks First, and Reasonable Price.Guanchen will be your faithful partner from China.
Type C To Network Adapters,Type-C To Network Hubs Rj45 Adapter,Network Hubs Rj45 Adapter,Usb-C To Gigabit Network Adapter
Shenzhen GuanChen Electronics Co., Ltd. , https://www.gcneotech.com