In these two days, the NSA hacked incident (or Formula Event) or The Shadow Brokers (translated by the media in China as "Shadow Broker") is still in full swing. I am afraid that many small partners have already read a lot of reports. If you missed the details of the incident, it wouldn't matter. This article will help you sort through the ins and outs of the NSA’s hacked case, as well as these popular vocabularies. What means.
Last week, a group of hackers claimed to invade the NSA, that is, the US National Security Agency - in fact, only to see the words "NSA was hacked" was enough shocked. The NSA was the protagonist of the Prison Gate incident two years ago. This agency is affiliated with the U.S. Department of Defense and is the largest intelligence agency in the U.S. government agencies. It is responsible for collecting and analyzing communication data (including foreign countries).
When the Prism Door incident broke out, former NSA employee Edward Snowden disclosed a large number of jaw-dropping NSA internal documents. The Swordsman NSA listened to U.S. nationals’ network activities through various means and even cooperated with technology companies, and their tentacles also extended. Go abroad.
This time, it was actually the goal of the NSA being hacked and hacked, specifically the NSA's Equation Group. Is this equation organization a skeleton organization? As early as February 2015, Kaspersky Lab released a research report, pointing out that since 2001, there has been a hacker organization within the NSA. Kaspersky named the organization an equation organization.

The characteristic of the equation is that it employs "complex" 0-day malicious programs to launch intelligence spying activities targeting all walks of life. According to Kaspersky's report, the equation organization combines a variety of sophisticated and high-end strategic tactics, techniques, and highly consistent processes. There are many sophisticated intrusion tools within the organization - it is said that these tools need to spend a lot of energy to develop.
Kaspersky’s peer organization’s evaluation was quite “high†at the time: the complexity and refinement of the technology used by this secret organization “surpassed any known intelligenceâ€. For example, before the emergence of the famous Stuxnet Seismic Network and the Flame Flame Virus, the 0-day loopholes involved have already been used for the equation - and the equations are also linked to the behind-the-scenes promoters of these malicious activities. For example, Fanny's malicious program, which was already in use in 2008, was a new variant of Zhennet until 2009 and 2010.

The tentacles of the equation may reach even more tens of thousands of victims in more than 30 countries around the world. The fields of the "special care" equation include the government and diplomatic agencies, communications, aerospace, energy, petroleum, military, nanotechnology, nuclear research, mass media, transportation, finance, companies that develop encryption technologies, and Muslims. Students interested in the other program can read Kaspersky’s report.
One of the APT organizations of such a sirloin turned out to be black by others! ?
Question 2: Who has been black?The hacking organization inside this intrusion equation is called The Shadow Brokers . This is actually the exact information of the attacker who has already mastered the name "The Shadow Brokers".
Question 3: What is the purpose of intrusion?As we mentioned earlier, the equations have developed a variety of high-end intelligence theft tools, and most of them use a variety of products, including 0-day loopholes in security products to invade. So after stealing the NSA equations, The Shadow Brokers stole a lot of tools from this organization. To be exact, it was posted on the Internet on the 13th of this month (GitHub and Tumblr, but it has been deleted ), including malicious programs, hacking tools, exploit tools, etc.
However, The Shadow Brokers has divided these tools into two parts, some of which are free to download and trial, and some (there are said to be the remaining 40% of the best files) are priced for sale at a price of 1 million bitcoins (about 578 million U.S. dollars). Funny! Buying a company is also money.) GitHub quickly deleted the relevant pages, but it's interesting that the reason for the deletion was not government pressure, but GitHub's policy does not allow the sale of stolen assets.
Looking at the behavior of this bright side, can we think that the purpose of The Shadow Brokers is actually for money ?

When things have developed to this point, what the safety practitioners most want to know is whether the published documents are true and reliable. It was only in the fermentation of the following days that people felt very scary. First of all, Kaspersky came forward to confirm that these documents are absolutely true and valid (the terms used in foreign media are legitimate) , and from all kinds of signs, are related to the organization of equations.
Researchers at Kaspersky Lab have published details of the study of these materials:
The size of the data that The Shadow Brokers publicly provides for free download is about 300MB. It contains specific exploits, hacking tools, and scripts for certain firewall products. The specific names of the tools are BANANAUSURPER, BLATSTING, and BUZZDIRECTION. However, these documents have a history of at least 3 years. The latest timestamp was marked in October 2013.
So what on earth is it related to the equation? Kaspersky Lab mentioned: "Although we can't determine the identity or motivation of the attackers, we don't know where or how these tools come from, but we can make it clear that the leaked hundreds of tools and equations are organized. There is definitely a close connection."
The Shadow Brokers publishes approximately 300 files in its documentation, using RC5 and RC6 encryption algorithms as common strategies, methods, and equations.
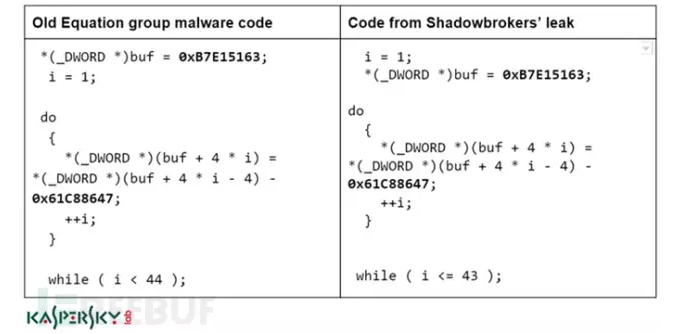
"The similarity of its code has given us a high degree of certainty that the tools leaked by The Shadow Brokers and the malicious programs of equations are indeed related." The figure above is an earlier version of the RC6 code, and the leaked documents in The Shadow Brokers this time Code, the same functions, constraints, and some of the more rare features are very illustrative.
In addition to Kaspersky, the former staff of the NSA's other mystery organization, TAO (Specific Intrusion Action Office), also believes that these tools are the same tools used for the equations. The Washington Post has also reported this.
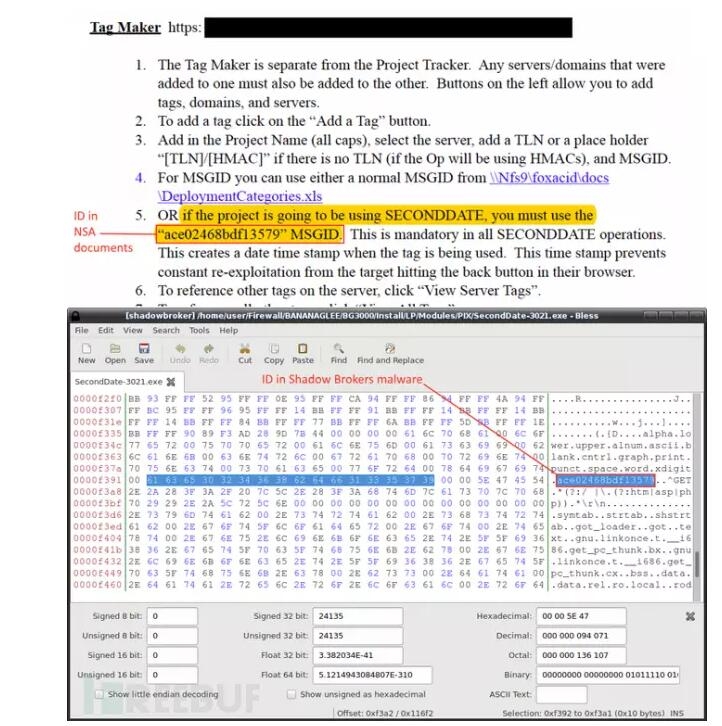
On Friday, The Intercept released a new round of Snowden leaked documents. There are many tools associated with this leaked tool. These are all evidences: For example, Snowden disclosed a document containing a SECONDDATE utility. This tool can interfere with web requests at the network layer and redirect it to the FOXACID server. On page 28 of the “Operation Manual†mentioned that NSA employees must use IDs to mark victims sent to the FOXACID server. For ace20468bdf13579, this ID appeared in 14 different files that The Shadow Brokers leaked.
We can also give some examples of how these tools can be used. For example, security researchers tested the EXTRABACON utility and confirmed that using this tool, they can access the Cisco firewall without providing a valid credential. : This tool utilizes the 0-day vulnerability in the Cisco ASA software's SNMP protocol (CVE-2016-6366), which can cause "unauthorized remote attackers" to fully control the device.
In addition, there are 0-day exploits that exploit some of Cisco's earlier vulnerabilities, such as exploiting the Cisco CVE-2016-6367 vulnerability, which exists in the command-line interface resolver of the Cisco ASA software and can cause unauthorized localities. The attacker constructed the DoS attack conditions and the risk of executing arbitrary code—the leaked EPICBANANA and the JETPLOW tools exploited this vulnerability.

As another example, there is a tool that can decrypt Cisco PIX VPN traffic and implant malicious programs in the firmware of the motherboard. This attack method is almost impossible to detect and cannot be deleted.... This affected vendors include Cisco, Juniper, Fortinet, etc., it is worth mentioning that leakage tools also contain exploit tools for domestic TOPSEC firewall products. Cisco actually confirmed the existence of these vulnerabilities for the first time, and released corresponding patches - think about it, the time stamp of the leaked files mentioned above was at least 3 years ago. It can be imagined that these 0day vulnerabilities have More 0day.
FreeBuf has also recently published several articles on parsing leaked documents, such as this one: "NSA (National Bureau of Security) Leaky Document Depth Analysis (PART 1)", these are essentially the expression of how terrifying the equation.
Question 4: Is it really about 1 million bitcoins?Regarding this issue, there are many opinions in the industry. To answer this question, it is necessary to figure out who is behind the scenes of the attack. There are two main current attitudes. The first is the internal staff of the NSA (the language of the foreigner is the insider's job) — This is what the industry's famous Matt Suiche said. He said that he talked with former NSA TAO employees about this matter. He wrote this in his blog:
"This leaked document actually contains the NSA TAO toolkit. These tools were originally stored on a physically isolated network and would not have access to the Internet at all."
"Those files have no reason at all to be on the staging server server unless someone deliberately does so. File-level relationships, as well as file names, have not changed. This should indicate that these files were copied directly from the source."
In addition to thinking that it was internal staff, Snowden had a special voice on Twitter about this matter. He thinks this is "Russia's response to the United States." Although this "response" is a bit confusing, it is said to be directed against the United States. Condemned Russia's invasion of the DNC Democratic National Committee (Lol). In the first two weeks, WikiLeaks released a large number of internal documents from DNC (and another DCCC Democratic Congressional Committee). Many US security companies and intelligence agencies believe that this matter is related to Russia, although Russia has denied it.
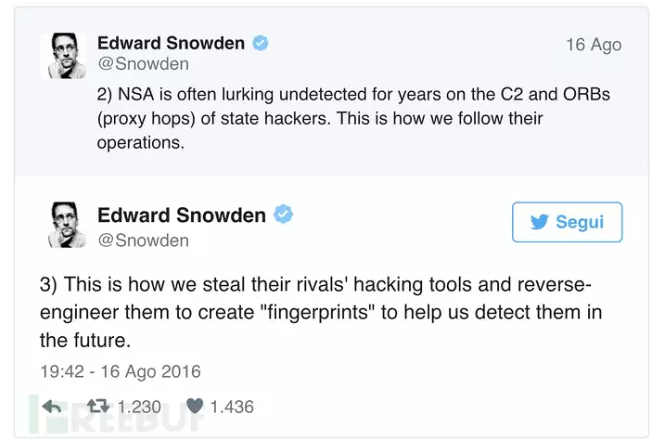
"This leak incident looks like someone sent a signal that this game will continue to expand rapidly. This is like a warning, and someone wants to prove that the United States is responsible for all the attacks launched by this malicious program server. This incident may have a great impact on foreign follow-up strategies, especially those targeting the United States and those outside the United States that want to target the United States."
From Snowden's point of view, intrusion equation servers are not that difficult for Russian hackers. Even if the NSA is backed by such complicated tools, the Russian network department has a very deep understanding of the NSA and has the ability to detect all attacks initiated by the NSA. He also said that these hackers did not get the data after June 2013, because that time coincided with Snowden announced the NSA's confidential documents, NSA is likely to replace this infrastructure.
Therefore, the mainstream view of foreign media believes that The Shadow Brokers' request for the 1 million bitcoin is just a smoke bomb. It is simply confusing. As for the truth, it is estimated that we need to wait for more analysis.
Question 5: How is the new progress?In fact, we still have a big problem that hasn't been resolved. This is how the Shadow Brokers intruded on the equation server. Of course, no one has yet been able to reveal this matter. The famous Italian researcher Claudio Guarnieri speculated that the hacking organization may have entered the “listening post†(listening station?), which is an integral part of the entire intelligence infrastructure of the equation.
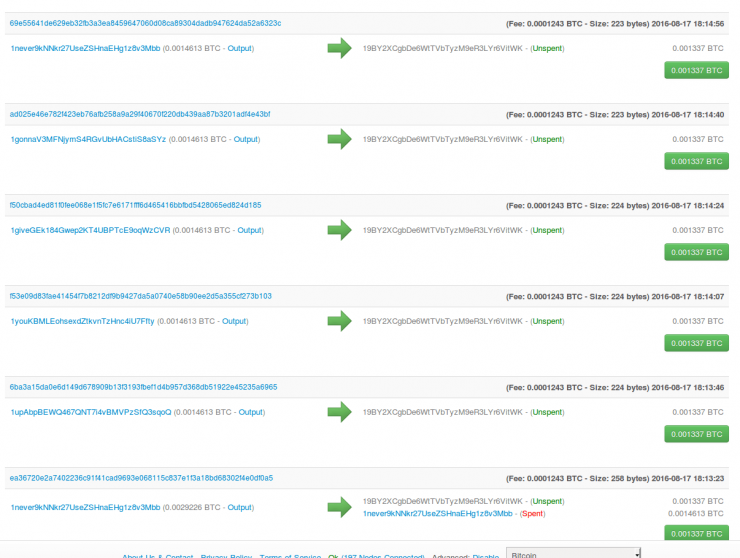
Strange transaction, 0.001337 bitcoins per pen
There is also the identity of The Shadow Brokers, which may also be a curiosity for many people. There is also an interesting thing: reports from Security Affairs that there was a very strange transaction on the Internet in the past two days, the Shadow Brokers account has undergone some changes, and a few days ago it imported about $990. What makes people feel weird is that this $990 comes from the Silk Road Bitcoin account. and many more! Isn't Silk Road Bitcoin already under FBI control (after the black market's arrest)? Not only that, but there are other accounts that send money (diversion?). This is a mystery!
The NSA hacking incident is still a problem. We will continue to wait for the event to be further fermented and follow-up reports. However, is there any security in the world?
Lei Fengwang Note: The author of this article Ouyang Ong, FreeBuf hackers and geeks (FreeBuf.COM) authorized the release of Lei Feng network (search "Lei Feng network" public number concerned) , reproduced please indicate the source and author, not to delete the content.
Gas Generator,4 Cycle 16 Cylinders,4 Cycle 16 Cylinders Cummins Generators,4 Cycle 16 Cylinders Generators
XCMG E-Commerce Inc. , https://www.xcmg-generator.com